select the best answer. which of the following are breach prevention best practices
The following are high-level best practices for preventing breaches. Which of the following are breach prevention best practices.

6 Best Practices For Protecting Client Confidentiality Titanfile
Which of the following are breach prevention best practices.

. Select the best answer. 10 best practices for data breach prevention 1. Identify users with access to sensitive data.
Elements of a risk analysis include. When must a HIPAA. This guide covers ways to best equip your.
The following best practices may help. Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Companies that leveraged artificial intelligence machine learning analytics and automated.
Which of the following are breach prevention best practices. 10 best practices for data breach prevention 1. Select the best answer.
30 Best Practices for Preventing a Data Breach. Best practices for breach prevent are. Invest in security automation.
Logoff or lock your workstation when it is unattended. Which of the following are breach prevention best practices Saturday June 11 2022 Edit. Endpoint breach prevention is needed not only to fulfill legal requirements but for the issues well in the next section we are going to cover best practices which are needed to achieve endpoint they do not have a realization of the fact a data breach response framework has a crucial role in handling.
And privacy officials select reasonable and appropriate protections for ePHI that satisfy current policy requirements. See answer 1 Best Answer. One of the most common causes of a data breach is weak password policies.
All of the above A breach as defined by the DoD is broader than a HIPAA breach or breach defined by HHS. Check spelling or type a new query. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Which of the following are breach prevention best practices. Train Employees on Security Awareness. Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System.
There are Microsoft best practices best practices and practices. Select the best answer. Conduct a risk assessment before any solution is implemented it is important to know your networks 13.
Promptly retrieve documents containing PHIPHI from the printer. Select the best answer. Promptly retrieve documents containing PHIPHI.
1 who has lead responsibility. Access only the minimum amount of PHIpersonally. Select the best answer.
Silahkan kunjungi postingan which of the. Which of the following are breach prevention best. Hipaa health insurance portability and accountability act is a legislation.
Logoff or lock your workstation when it is unattended. Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion. The employees play an essential responsibility in keeping their companies safe.
Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. Identity sensitive data collected stored transmitted or processes. You should always logoff or lock your workstation when it is unattended for any length of time.
Which of the following are fundamental objectives of information security. If theyre not aware of security and appropriate education they could be the weakest connection in the security of the data chain and create a significant. All of this above answer.
The typical steps most cybercriminals follow during breach operations are. Identify areas that store transmit collect or process sensitive data. Discuss best practices for preventing breaches.
All of this above. Best practices for breach prevent are. What are breach prevention best practices.
Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices. Identify devices that store transmit collect or process sensitive data.

7 Key Steps To Investigate A Data Breach With Checklist Ekran System
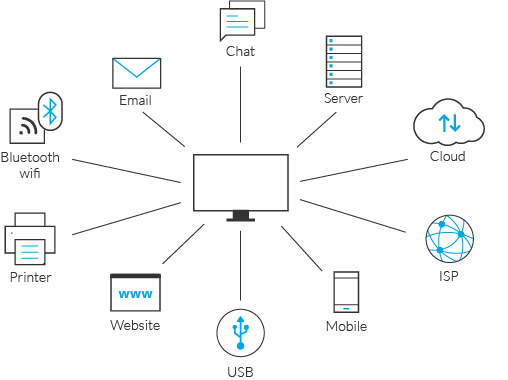
What Is Data Loss Prevention Dlp Data Leakage Mitigation Imperva
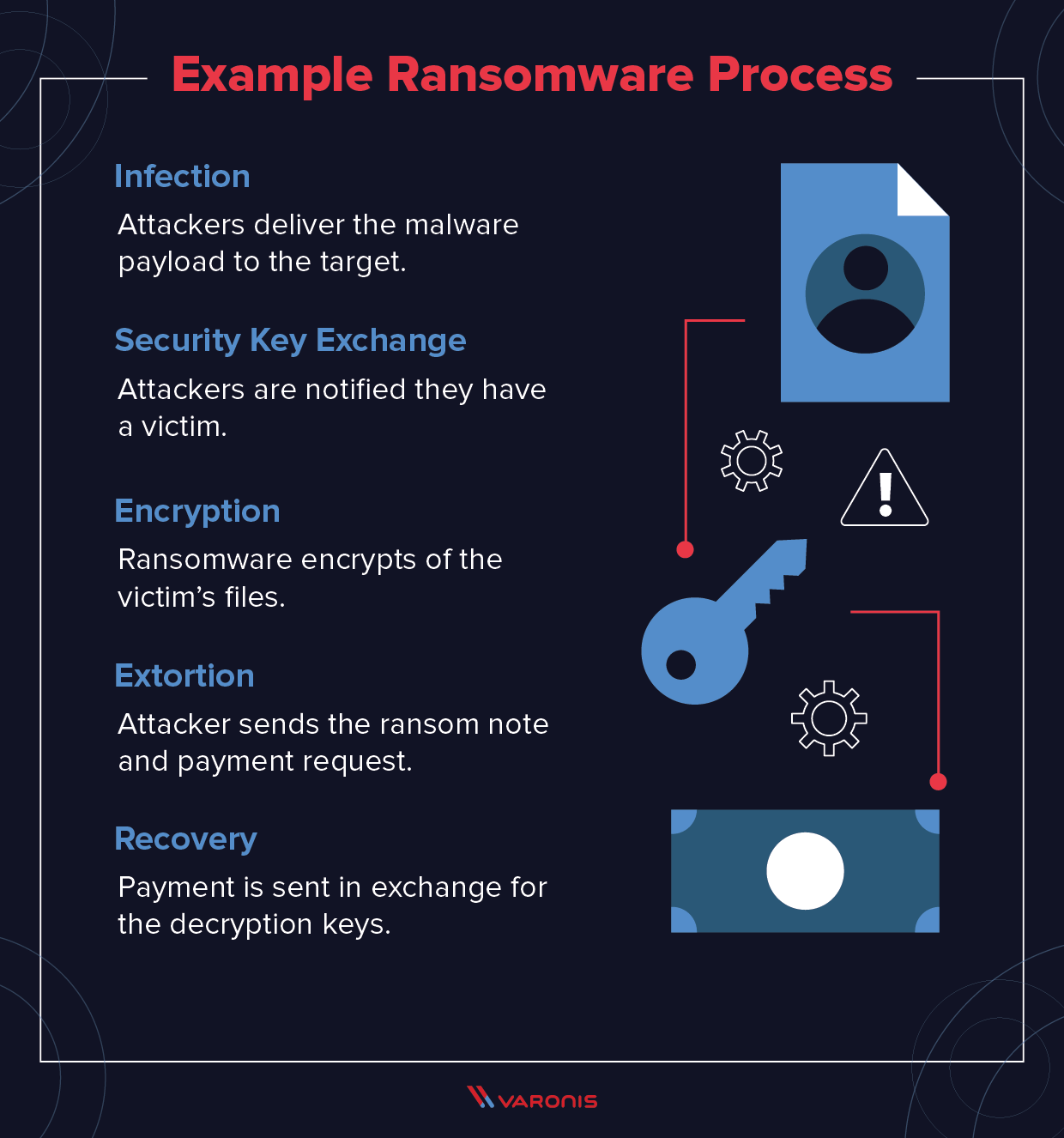
How To Prevent Ransomware The Basics
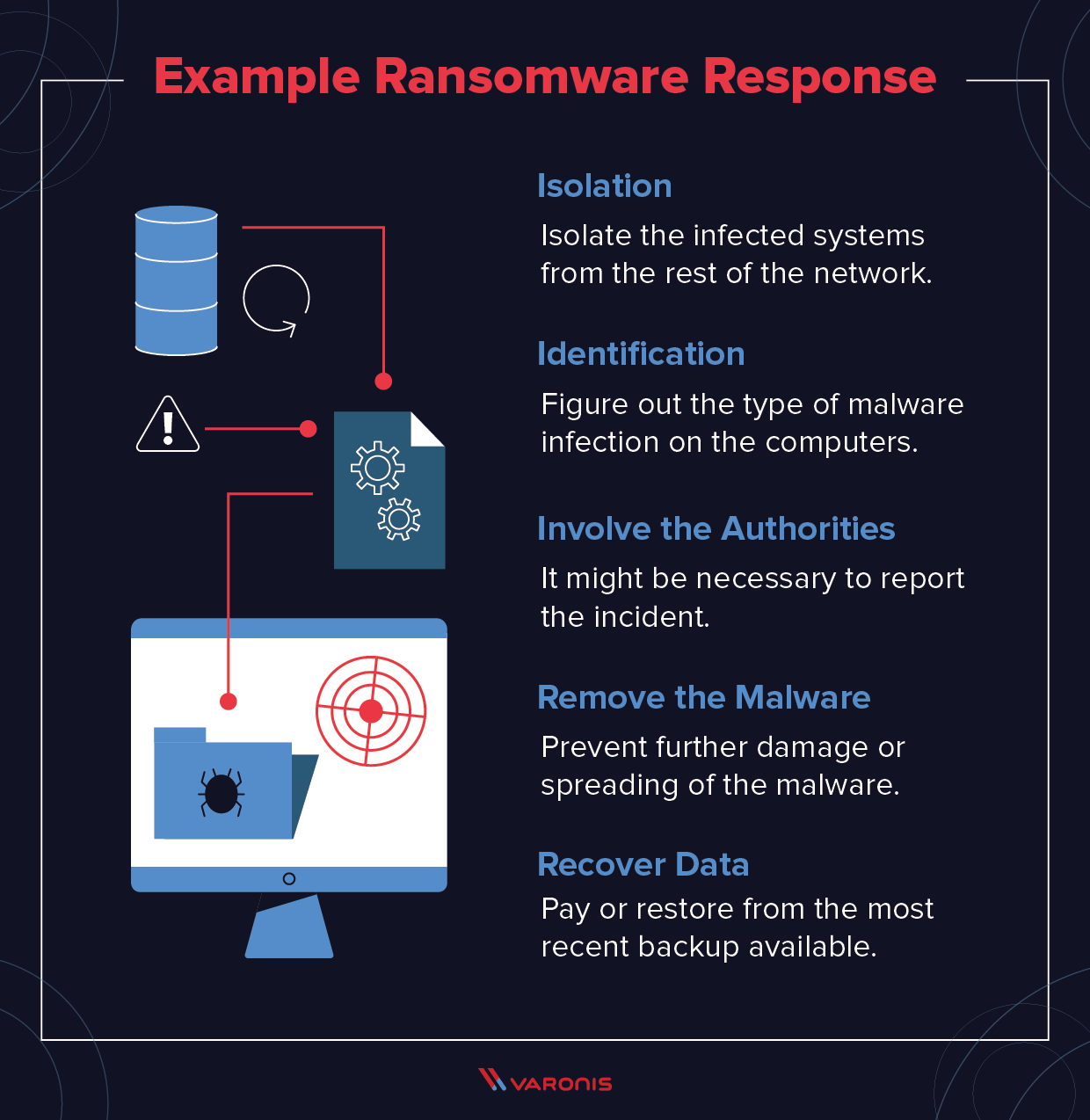
How To Prevent Ransomware The Basics
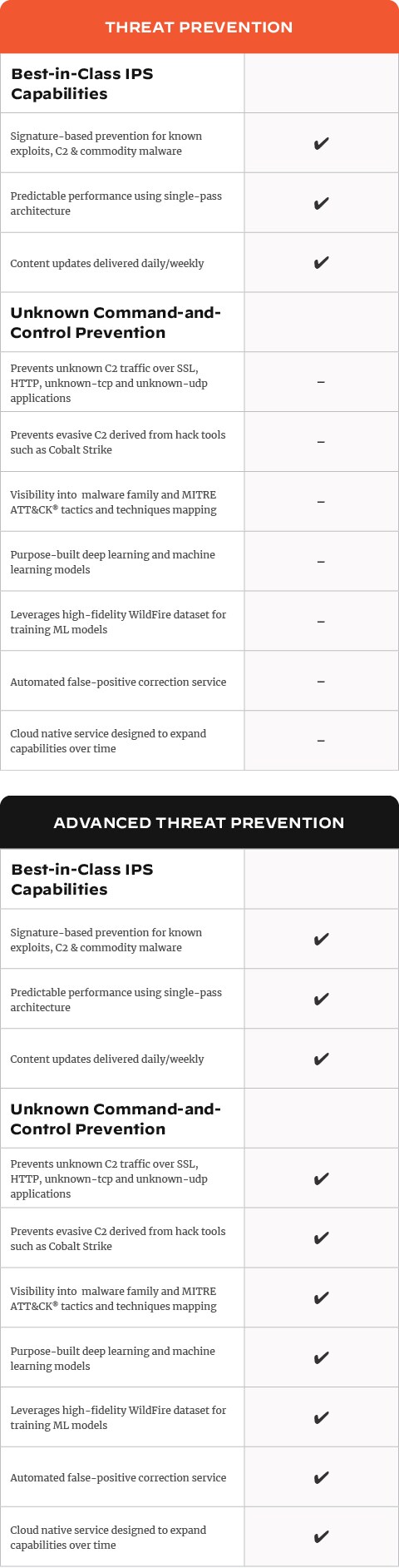
Threat Prevention Palo Alto Networks
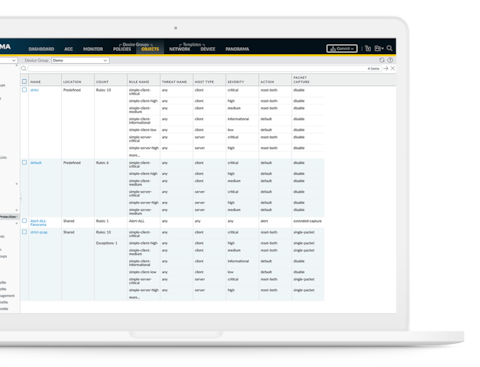
Threat Prevention Palo Alto Networks

The 10 Data Security Measures You Must Take For Your Business Wimi

Top 5 Internal Data Security Threats And How To Deal With Them Endpoint Protector
Frequently Asked Questions About Data Loss Prevention Endpoint Protector

Data Security Definition Explanation And Guide

6 Steps Colleges And Universities Can Take To Protect Against Cyber Attacks Part 2 Fierce Education

Top 5 Internal Data Security Threats And How To Deal With Them Endpoint Protector

Net Broken Access Control Guide Examples And Prevention

7 Reasons Why Security Awareness Training Is Important Cybsafe

Equifax Aftermath How To Protect Against Identity Theft Identity Theft Protection Identity Theft Identity Fraud

What Is Application Security Vmware Glossary

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

How To Protect Your Data At Rest Endpoint Protector

What Is Data Loss Prevention Dlp Beginners Guide Crowdstrike